We all know that security is important, but we are usually too lazy to add basic security. In this tutorial I will show you how to secure a Linux server in 3 simple steps, starting from basic to more advanced security.
This requires a VPS, if you do not already have a VPS, you can get one from HostUp starting from $3.00/mo – View plans, or visit our Swedish languaged site at hostup.se
1. Create a New Account
This is not really a security ‘feature’, but it is always a good idea to either move away from root or setup login with authorized keys since the most common username out there is root since it is the default. For this reason, most brute-force programs tend to try to use that username.
When you have logged into an SSH terminal with your specified username & password proceed with the following commands to create a new root privileged account. Change changeme with what username you want the account to have.
Create the new account:
adduser changeme
Give the account root privilege:
usermod -aG sudo changeme
Switch over to your newly created user account:
su – changeme
After you have created your new account you may start a new SSH session, only this time connect with your new username & password.
2. Replace Password Login With Authorized keys
Stop using passwords all together when logging into your Linux server, and replace it with public and private authentication keys instead!
Step 1.
Generate your 2048bit public and private keys via a generator such as PuttyGen. If you do not already have it you may download it from putty.org
Click the Generate button marked with red. You can open this window by simply searching PuttyGen in the Windows search box.
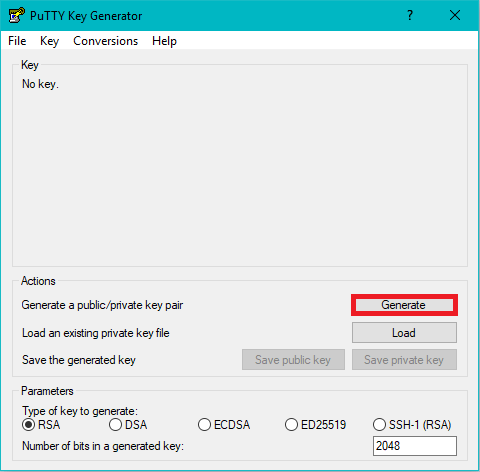
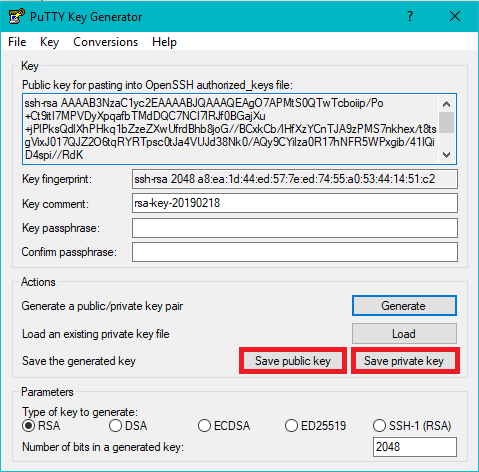
You are now ready to start using your newly generated keys. Open up the contents of your public key with an editing tool such as NotePad++. Back on your SSH client, run the following commands
Step 2.
First we want to make a new directory called ssh:
mkdir .ssh
After this we want to create a file called authorized_keys where we will be putting our public key inside
nano .ssh/authorized_keys
If you do not have nano install then please proceed to installing it by running the following command:
sudo apt-get install nano
You should put your public key in like this:
ssh-rsa KEYHERE
Example of this being:
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEApLqp8zeP5y/7GQ99ml6325WeSr+j+vpBxi/0YJzTgz1xkILXwjaikLaaNPP5dp7fAVyBAjl3XqlAnng7yh4KVqWSgga8drlfj1ljyzQHPeCib6pLlgyyZbh4L/YaWjvcKfj5YK13hCUuKiHMUa69QZHmX+tT+iKr9ax49xPILGHJK8n1/V0lYg+C+z35cS9EbHMJRP3Kx2vWFPaFkJr6OxN4N0HK3ZLYv4wdUHQbeG9Ahzj8c8iQGSgMy5lVIvlwZJAn4xE8XqjAKW7dVFwKeVciesR+HjQVvqdCq18z9fmSGN5i/YbPfSUOKgxgtBChswf/7BdV8XFby5Xk+hRUQ==
After this, save and exit by pressing
chmod 600 .ssh/authorized_keys
Step 3.
Next we want to disable password authentication and only allow authentication using our newly created private and public key.
First we want to open your sshd_config configuration file:
nano /etc/ssh/sshd_config
FindPasswordAuthentication yes and replace it with PasswordAuthentication no to disable password logins
If you feel like disabling root logins:
Find PermitRootLogin yes and replace it with PermitRootLogin no
Again, save and exit by pressing
Restart SSH:
sudo service sshd restart
Congratulations, you have now disabled root & password logins. To login into the server in the future, you will need to use your private key. In Putty SSH client you can add this by going to:
Connection > SSH > Auth and selecting your private key in the browse tab.
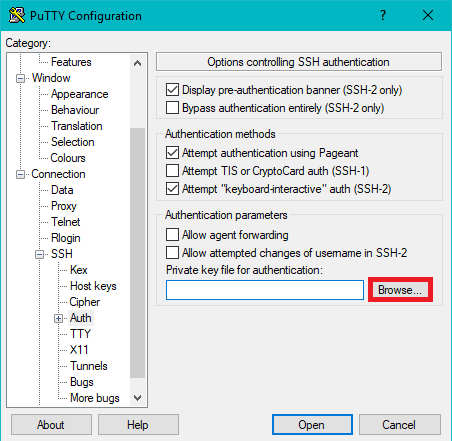
3. Install a Firewall on Your Linux Server
It is highly recommended that you install a firewall and only allow for ports that you actually use.
sudo apt-get install ufw -y
sudo ufw allow ssh/tcp
sudo ufw limit ssh/tcp
sudo ufw logging on
sudo ufw enable
You can add additional ports by running the command:
sudo ufw allow PORTHERE/tcp
Remember to replace PORTHERE with your specified port.
Another good thing to install is Fail2ban. Fail2ban will monitor your firewall logs and ban any IPs that act suspiciously.
To install Fail2ban firstly:
sudo apt -y install fail2ban
After you have install your very own installation of Fail2ban, you want to make sure that it starts automaticly on restart:
sudo systemctl enable fail2ban
All you have got left to do is to start the program:
sudo systemctl start fail2ban
Congratulations! If you have made it this far you can be sure that your Ubuntu server is fully secured. Remember to share this tutorial to anyone who wants to have a more secure server and bookmark. It is better to be safe that sorry afterall :).
 English
English
 Swedish
Swedish